I have been pretty busy going through the Google Cybersecurity Professional Certificate as of late, I'm currently at course number 3 - Connect and Protect: Networks and Network Security, and I had been assigned to create a security incident report.
In this scenario, a website has been compromised and an attacker executed a brute force attack to gain access to the web host, from there he was able to access the admin panel and inject a javascript function into the code of the website that downloads a malicious file that redirects the website from the original address into the attacker's custom website address.
I first started by going over the tcpdump logs, and of course, when trying to access the website it immediately downloads the malicious file:
Upon re-entering the website, it changed from the original URL to a different one thus assuring that the malware has done its job.
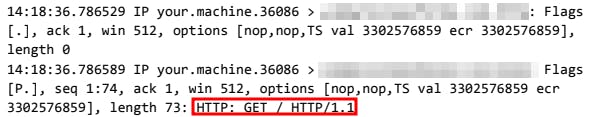
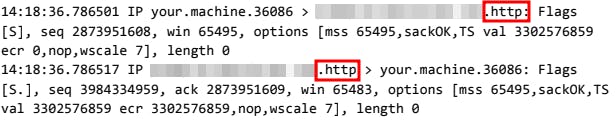
So inspecting the logs further we can see that the involved network protocols are DNS and HTTP:
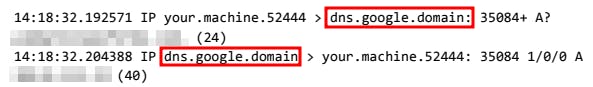
DNS referring to the DNS server when entering the website URL, translating it into a valid IP address.
After doing so I documented the incident - At around 14:18 we can see that the DNS server translates the website address into the original IP
upon entering the website less than a second later an HTTP GET request is seen, it is suspected that this request is for downloading the malicious file using HTTP at the application layer.
2 minutes later at around 14:20, we can see that our machine is asking the DNS server for a different address and we are greeted with a different IP.
This shows that after the malware has successfully run, it automatically redirects our machine to the attacker’s website.
You can view the full report here, this assignment was a lot of fun and was great practice for reading tcpdump logs.

